EndPoint Security
Product Description -
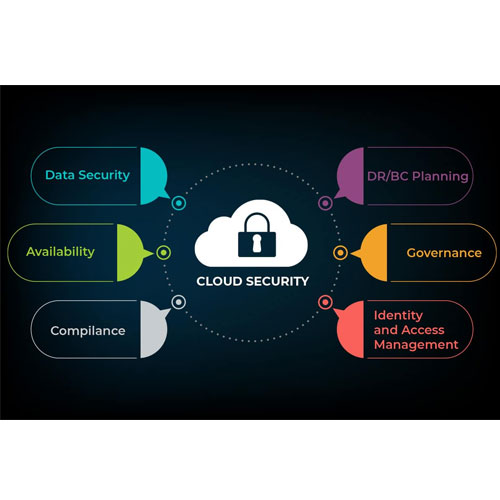
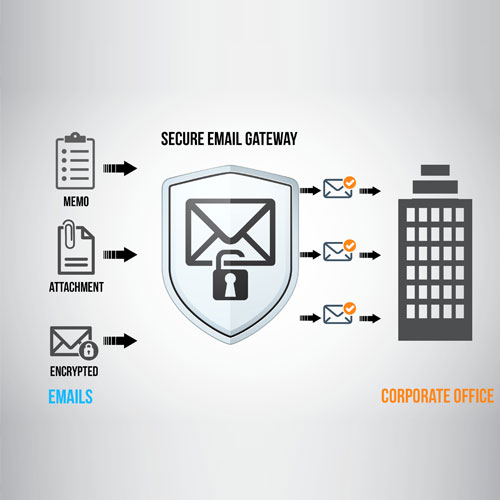
Endpoint security safeguards devices like laptops, desktops, and mobiles from cyber threats. It involves using software to detect and prevent attacks such as malware and ransomware. Modern solutions go beyond antivirus, offering advanced protection against sophisticated threats. By monitoring endpoints, organizations can identify and respond to incidents quickly, reducing damage. It's a crucial layer of defense in today's threat landscape.
20 Products sold in last 12 hours
Only 10 Left !
Quantity
Guranteed Safe Checkout
Product Description -
Endpoint security safeguards devices like laptops, desktops, and mobiles from cyber threats. It involves using software to detect and prevent attacks such as malware and ransomware. Modern solutions go beyond antivirus, offering advanced protection against sophisticated threats. By monitoring endpoints, organizations can identify and respond to incidents quickly, reducing damage. It's a crucial layer of defense in today's threat landscape.
Product Specification -
| Feature | Description |
|---|---|
| Definition | Endpoint Security refers to the practice of protecting endpoints, such as computers, mobile devices, and servers, from cyber threats and unauthorized access. |
| Key Components | - Antivirus and anti-malware - Firewall protection - Intrusion detection and prevention - Data encryption - Endpoint detection and response (EDR) |
| Security Measures | - Regular updates and patches - User authentication and access controls - Continuous monitoring for threats - Incident response and recovery plans |
| Benefits | - Protects sensitive data - Reduces the risk of data breaches - Enhances compliance with regulations - Provides remote management capabilities |
| Deployment Models | - On-premises solutions - Cloud-based solutions - Hybrid approaches |
| Target Users | - Businesses of all sizes - Managed service providers (MSPs) - IT departments |
| Common Threats Mitigated | - Malware and ransomware - Phishing attacks - Data breaches - Insider threats |
| Compliance Standards | - GDPR, HIPAA, PCI-DSS, and other industry-specific regulations |
Related Products